34+ intrusion detection system diagram
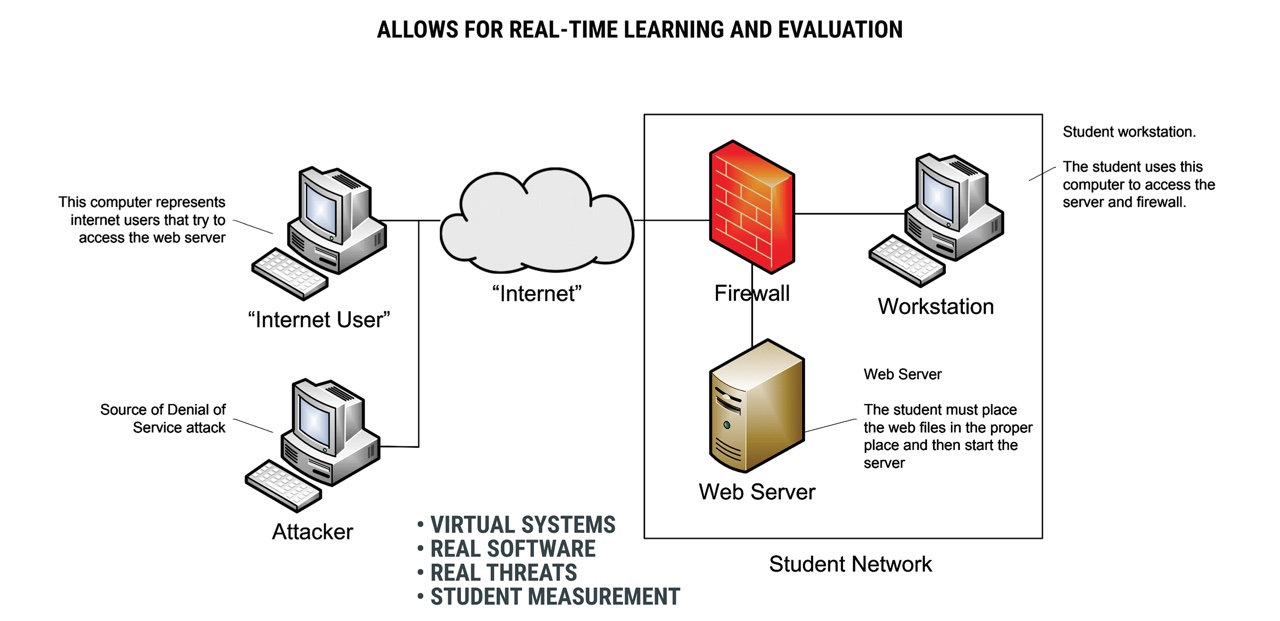
The basics of a IDS is if there is an attack on the network the IDS is going to be sitting there and analyzing. To implement Intrusion Detection System with the help of Face recognition in terms of motion.

Thinkcar Obd2 Scanner Thinktool Mini Oe Level Full Systems Automotive Diagnostic Scan Tool With 28 Reset Car Scanner Lifetime Free Update Immo Key Programming Ecu Coding Bidirectional Scan Tool Code Readers Scan Tools
An Intrusion Detection System IDS can be used to detect attacks on CAN.
. General-purpose intrusion-detection expert system. Intrusion detection system classic by Nikhil Aggarwal. Download scientific diagram Intrusion detection system discussed 34.
Use Createlys easy online diagram editor to edit this diagram collaborate with others and export results to. New users enjoy 60 OFF. Business photo text monitors a network or systems for malicious activity Presentation of Bar Data and Pie Chart Diagram Graph Each on White.
The IDS sends alerts to IT and security. Intrusion Detection System is a software application to detect network intrusion using various machine learning algorithmsIDS monitors a network or. An intrusion detection system IDS is software specifically built to monitor network traffic and discover irregularities.
It can however log messages generated by Windows. An intrusion detection system IDS is an application that monitors network traffic and searches for known threats and suspicious or malicious activity. Unwarranted or unexplained network changes could indicate.
Download 99 Diagram Intrusion Detection System Stock Illustrations Vectors Clipart for FREE or amazingly low rates. INTRODUCTION 11 Purpose The aim of the project is to. 191798951 stock photos online.
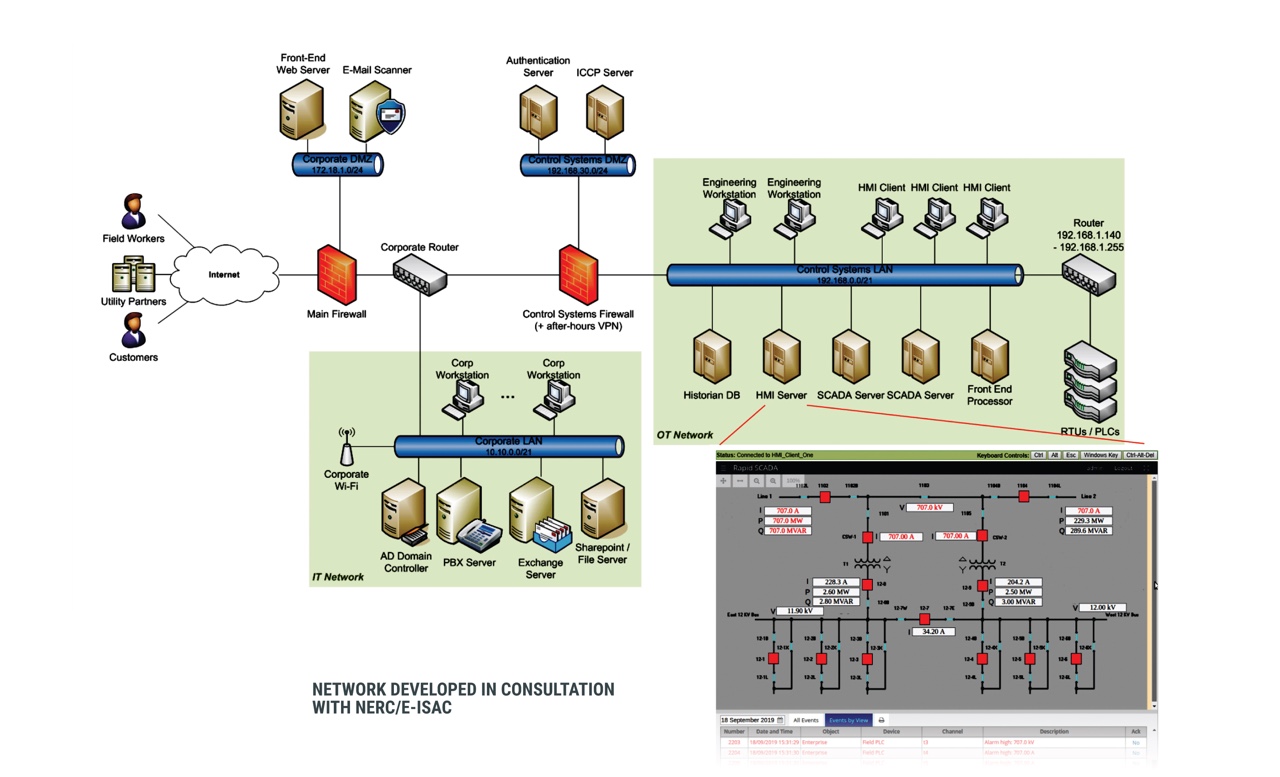
Intrusion Detection System for the Internet of Things Based on Blockchain and Multi-Agent. Introduction This paper describes a model for a real-time intrusion-detection expert system that aims to detect a wide range of. Intrusion Detection Systems were available before Intrusion Prevention Systems.
Machine learning for the IDS in particular would be useful for creating models to detect non-linear attack patterns. Text sign showing Intrusion Detection. When an intrusion detection system is designed the wiring configuration used can vary depending on building size building use infrastructure complexity specifier familiarity.
SolarWinds Security Event Manager SEM is an intrusion detection system designed for use on Windows Server.
2
A Survey Of Artificial Intelligence Techniques For Cybersecurity Improvement Document Gale Academic Onefile

Amazon Com Topdon Phoenix Pro Ecu Ecm Programming Scan Tool Bi Directional Control All System Diagnostic Scanner Online Coding 34 Maintenance Service Oe Level Diagnosis 2 Years Free Update Automotive
A Survey Of Artificial Intelligence Techniques For Cybersecurity Improvement Document Gale Academic Onefile
2
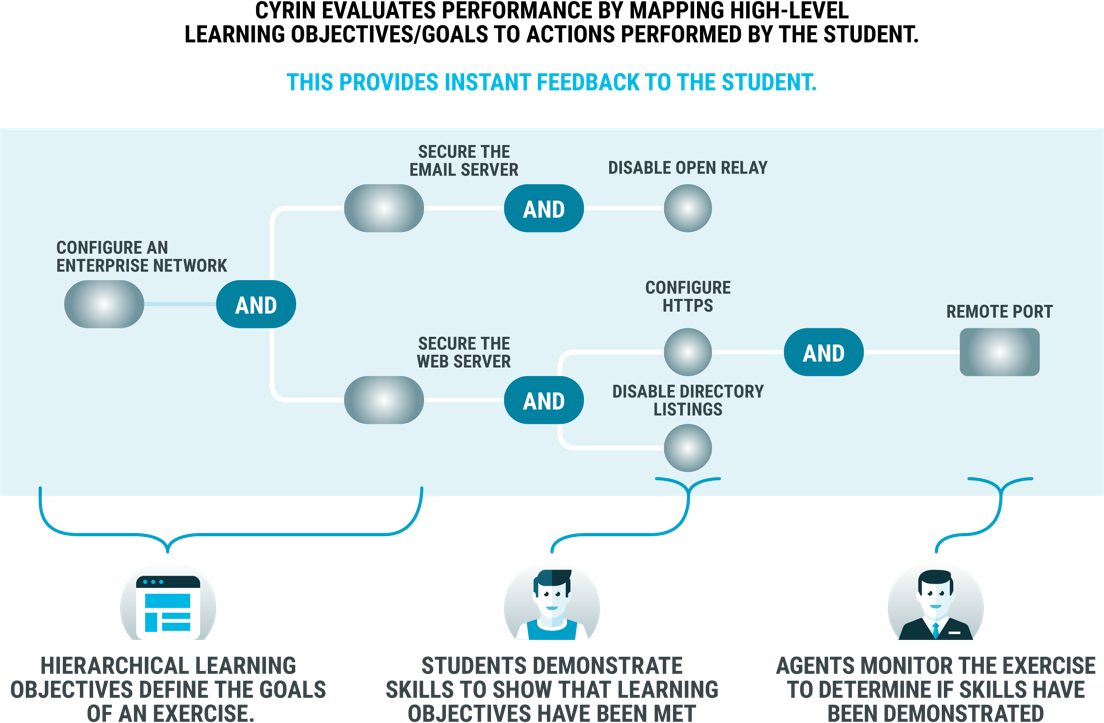
Cyrin Resources

Fiber Optic Cable An Overview Sciencedirect Topics
A Survey Of Artificial Intelligence Techniques For Cybersecurity Improvement Document Gale Academic Onefile

Fiber Optic Cable An Overview Sciencedirect Topics
2
Cyrin Resources
2

Fiber Optic Cable An Overview Sciencedirect Topics

Cyrin Resources

Fiber Optic Cable An Overview Sciencedirect Topics

Thinkcar Obd2 Scanner Thinktool Mini Oe Level Full Systems Automotive Diagnostic Scan Tool With 28 Reset Car Scanner Lifetime Free Update Immo Key Programming Ecu Coding Bidirectional Scan Tool Code Readers Scan Tools
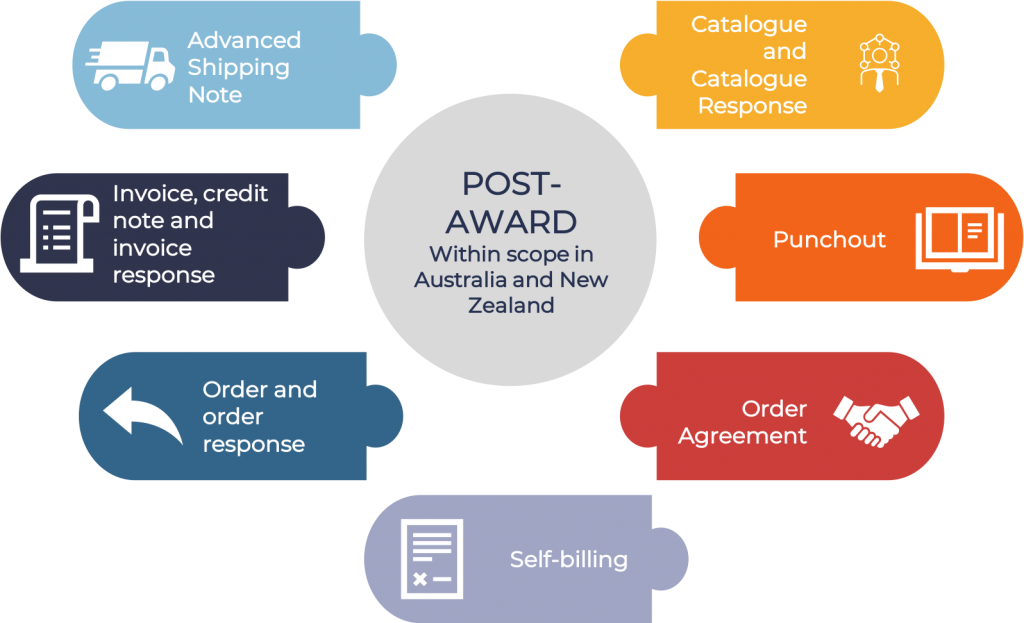
What Is Peppol A Simplified Guide To All Things Peppol